Microsoft Patch Tuesday August 2025 delivers critical security updates, fixing one zero-day vulnerability and addressing 107 flaws across Windows, Office, and Azure. Learn what’s new, why it matters, and how to protect your systems.

The Microsoft Patch Tuesday August 2025 security updates have arrived, and this month’s release is one of the more significant ones in recent memory. With 107 vulnerabilities patched — including one actively exploited zero-day flaw — Microsoft is urging all users, from home PCs to enterprise servers, to update immediately.
The August batch addresses critical flaws across Windows 10, Windows 11, Windows Server, Office, and other Microsoft products. Security experts are already calling this month’s updates “essential” due to the severity of the vulnerabilities and the broad attack surface they cover.
Table of Contents
A Quick Overview of the August 2025 Microsoft Patch Tuesday
On August 12, 2025, Microsoft rolled out patches for 107 security vulnerabilities. Out of these, 9 were rated Critical, 98 Important, and 1 was actively exploited in the wild before the patch. According to the official Microsoft Security Response Center (MSRC), the updates target flaws in components such as:
- Windows Kernel
- Windows TCP/IP stack
- Windows Hyper-V
- Microsoft Office
- .NET Framework
- Windows Server 2025
- Microsoft Edge (Chromium-based)
Security professionals emphasize that the zero-day vulnerability is the most pressing concern for both individual users and organizations.
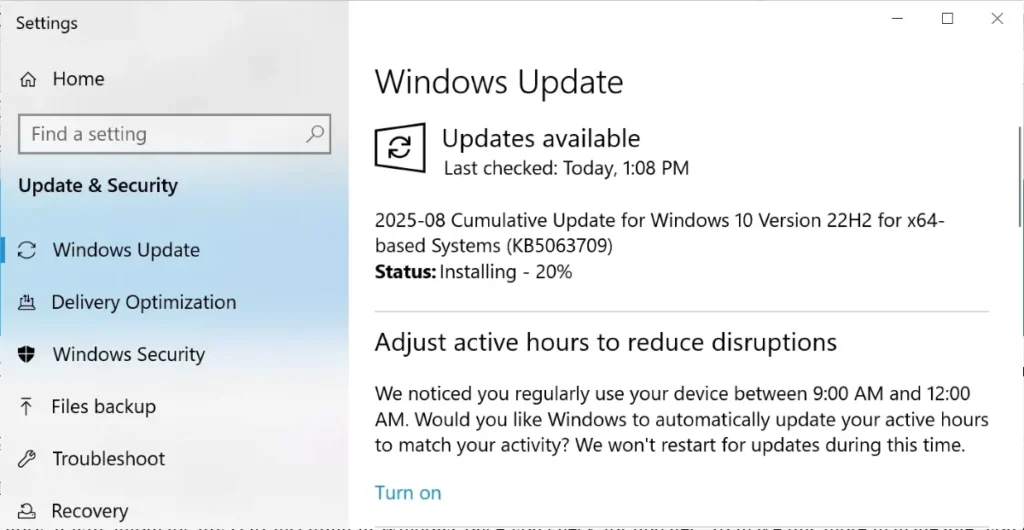
The Actively Exploited Zero-Day Vulnerability
The headline flaw this month is tracked as CVE-2025-30127, a privilege escalation vulnerability in Windows Kernel that allows attackers to gain SYSTEM-level privileges. According to BleepingComputer’s coverage, the bug has already been used in targeted attacks, making it urgent for all Windows devices to be patched.
If exploited, this vulnerability could allow cybercriminals to bypass security controls and install malicious programs, steal sensitive data, or create new admin accounts. Given the high risk, the US Cybersecurity and Infrastructure Security Agency (CISA) has also issued a security alert urging organizations to apply the patch without delay.
Critical Vulnerabilities That Demand Immediate Attention
While the zero-day has drawn the most attention, nine other Critical-rated vulnerabilities also require immediate action. Some of the notable ones include:
1. Windows TCP/IP Remote Code Execution Flaw (CVE-2025-27891)
This vulnerability could allow an attacker to send specially crafted network packets to a vulnerable system, leading to remote code execution without user interaction. This kind of flaw is particularly dangerous for systems exposed directly to the internet.
2. Hyper-V Virtual Machine Escape (CVE-2025-28903)
A flaw in Windows Hyper-V could let a guest virtual machine escape to the host operating system. This is a major concern for cloud service providers and enterprises running virtualized workloads.
3. Windows Server 2025 Authentication Bypass (CVE-2025-27654)
CSO Online reports that this flaw in Windows Server 2025 could allow attackers to bypass authentication mechanisms and gain unauthorized access to network resources.
Updates for Windows 10 and Windows 11 Users
If you are on Windows 10 or Windows 11, the August 2025 cumulative updates not only patch vulnerabilities but also bring security improvements to system components. For example, the KB5063709 update for Windows 10 includes fixes for Extended Security Updates (ESU) enrollment issues, which previously blocked some organizations from extending support for legacy devices.
Microsoft has also patched vulnerabilities in Windows Print Spooler, BitLocker, and Windows Defender, all of which have historically been targeted by ransomware operators.
Microsoft Office and Other Product Fixes
The Microsoft Patch Tuesday August 2025 rollout also delivers important security fixes for Microsoft Office 2019, Office LTSC, and Microsoft 365 Apps. Several flaws in Office’s document parsing engines could allow remote code execution if a malicious file is opened.
Additionally, Microsoft Edge received updates to address security holes inherited from the Chromium engine, as detailed in the Edge Release Notes.
Why This Patch Tuesday Is So Important
While every Patch Tuesday matters, August 2025 stands out because:
- Actively exploited zero-day means attackers are already targeting vulnerable systems.
- The wide range of products affected increases the potential attack surface.
- Several remote code execution flaws require no user interaction to exploit.
- The Windows Server authentication bypass could be devastating for enterprise networks.
Delaying updates in such a scenario is essentially leaving the door wide open for cyberattacks.

How to Install the August 2025 Updates
For Home Users
- Go to Settings > Windows Update and click Check for updates.
- Install all available security updates and restart your computer.
For Enterprise and IT Admins
- Use Windows Server Update Services (WSUS) or Microsoft Endpoint Configuration Manager to deploy updates.
- Test patches in a staging environment before rolling out to production.
Best Practices for Patch Management
Applying updates is just one part of a robust cybersecurity strategy. Experts recommend:
- Regular Backups – Always keep offline backups before installing major updates.
- Update Prioritization – Patch critical and actively exploited vulnerabilities first.
- Vulnerability Scanning – Use tools to verify all systems are patched.
- Security Awareness Training – Educate users about phishing and malware threats.
For organizations with complex environments, automated patch management tools can significantly reduce the window of exposure.
Industry Reactions
Security researchers and industry analysts agree that Microsoft Patch Tuesday August 2025 is a pivotal update cycle.
“The sheer number of flaws and the presence of an actively exploited zero-day make this month’s patches non-negotiable,” said a senior analyst at a leading cybersecurity firm. “We’re seeing increased targeting of unpatched systems within hours of vulnerability disclosures.”
Given the global increase in ransomware activity and state-sponsored attacks, the urgency is understandable.
Final Thoughts
The August 2025 Microsoft Patch Tuesday underscores the ever-evolving nature of cybersecurity threats. With over 100 vulnerabilities fixed and one dangerous zero-day exploit neutralized, it’s a critical reminder for both individuals and organizations to stay on top of updates.
The takeaway is simple: patch now. Whether you’re a casual Windows 10 user, a Windows 11 power user, or an enterprise running Windows Server 2025, applying these updates immediately will close the door to multiple high-risk attack vectors.
If you want to dive deeper into the technical details, you can explore Microsoft’s official update guide, which lists all CVEs and associated products.
The August 2025 Patch Tuesday Security Updates
Below is the complete list of resolved vulnerabilities in the July 2025 Patch Tuesday updates.
| Tag | CVE ID | CVE Title | Severity |
|---|---|---|---|
| Azure File Sync | CVE-2025-53729 | Microsoft Azure File Sync Elevation of Privilege Vulnerability | Important |
| Azure Stack | CVE-2025-53793 | Azure Stack Hub Information Disclosure Vulnerability | Critical |
| Azure Stack | CVE-2025-53765 | Azure Stack Hub Information Disclosure Vulnerability | Important |
| Azure Virtual Machines | CVE-2025-49707 | Azure Virtual Machines Spoofing Vulnerability | Critical |
| Azure Virtual Machines | CVE-2025-53781 | Azure Virtual Machines Information Disclosure Vulnerability | Critical |
| Desktop Windows Manager | CVE-2025-53152 | Desktop Windows Manager Remote Code Execution Vulnerability | Important |
| Desktop Windows Manager | CVE-2025-50153 | Desktop Windows Manager Elevation of Privilege Vulnerability | Important |
| GitHub Copilot and Visual Studio | CVE-2025-53773 | GitHub Copilot and Visual Studio Remote Code Execution Vulnerability | Important |
| Graphics Kernel | CVE-2025-50176 | DirectX Graphics Kernel Remote Code Execution Vulnerability | Critical |
| Kernel Streaming WOW Thunk Service Driver | CVE-2025-53149 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability | Important |
| Kernel Transaction Manager | CVE-2025-53140 | Windows Kernel Transaction Manager Elevation of Privilege Vulnerability | Important |
| Microsoft Brokering File System | CVE-2025-53142 | Microsoft Brokering File System Elevation of Privilege Vulnerability | Important |
| Microsoft Dynamics 365 (on-premises) | CVE-2025-49745 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | Important |
| Microsoft Dynamics 365 (on-premises) | CVE-2025-53728 | Microsoft Dynamics 365 (On-Premises) Information Disclosure Vulnerability | Important |
| Microsoft Edge for Android | CVE-2025-49755 | Microsoft Edge (Chromium-based) for Android Spoofing Vulnerability | Low |
| Microsoft Edge for Android | CVE-2025-49736 | Microsoft Edge (Chromium-based) for Android Spoofing Vulnerability | Moderate |
| Microsoft Exchange Server | CVE-2025-25005 | Microsoft Exchange Server Tampering Vulnerability | Important |
| Microsoft Exchange Server | CVE-2025-25006 | Microsoft Exchange Server Spoofing Vulnerability | Important |
| Microsoft Exchange Server | CVE-2025-25007 | Microsoft Exchange Server Spoofing Vulnerability | Important |
| Microsoft Exchange Server | CVE-2025-53786 | Microsoft Exchange Server Hybrid Deployment Elevation of Privilege Vulnerability | Important |
| Microsoft Exchange Server | CVE-2025-33051 | Microsoft Exchange Server Information Disclosure Vulnerability | Important |
| Microsoft Graphics Component | CVE-2025-49743 | Windows Graphics Component Elevation of Privilege Vulnerability | Important |
| Microsoft Graphics Component | CVE-2025-50165 | Windows Graphics Component Remote Code Execution Vulnerability | Critical |
| Microsoft Office | CVE-2025-53732 | Microsoft Office Remote Code Execution Vulnerability | Important |
| Microsoft Office | CVE-2025-53740 | Microsoft Office Remote Code Execution Vulnerability | Critical |
| Microsoft Office | CVE-2025-53731 | Microsoft Office Remote Code Execution Vulnerability | Critical |
| Microsoft Office Excel | CVE-2025-53759 | Microsoft Excel Remote Code Execution Vulnerability | Important |
| Microsoft Office Excel | CVE-2025-53737 | Microsoft Excel Remote Code Execution Vulnerability | Important |
| Microsoft Office Excel | CVE-2025-53739 | Microsoft Excel Remote Code Execution Vulnerability | Important |
| Microsoft Office Excel | CVE-2025-53735 | Microsoft Excel Remote Code Execution Vulnerability | Important |
| Microsoft Office Excel | CVE-2025-53741 | Microsoft Excel Remote Code Execution Vulnerability | Important |
| Microsoft Office PowerPoint | CVE-2025-53761 | Microsoft PowerPoint Remote Code Execution Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2025-53760 | Microsoft SharePoint Elevation of Privilege Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2025-49712 | Microsoft SharePoint Remote Code Execution Vulnerability | Important |
| Microsoft Office Visio | CVE-2025-53730 | Microsoft Office Visio Remote Code Execution Vulnerability | Important |
| Microsoft Office Visio | CVE-2025-53734 | Microsoft Office Visio Remote Code Execution Vulnerability | Important |
| Microsoft Office Word | CVE-2025-53738 | Microsoft Word Remote Code Execution Vulnerability | Important |
| Microsoft Office Word | CVE-2025-53736 | Microsoft Word Information Disclosure Vulnerability | Important |
| Microsoft Office Word | CVE-2025-53784 | Microsoft Word Remote Code Execution Vulnerability | Critical |
| Microsoft Office Word | CVE-2025-53733 | Microsoft Word Remote Code Execution Vulnerability | Critical |
| Microsoft Teams | CVE-2025-53783 | Microsoft Teams Remote Code Execution Vulnerability | Important |
| Remote Access Point-to-Point Protocol (PPP) EAP-TLS | CVE-2025-50159 | Remote Access Point-to-Point Protocol (PPP) EAP-TLS Elevation of Privilege Vulnerability | Important |
| Remote Desktop Server | CVE-2025-50171 | Remote Desktop Spoofing Vulnerability | Important |
| Role: Windows Hyper-V | CVE-2025-50167 | Windows Hyper-V Elevation of Privilege Vulnerability | Important |
| Role: Windows Hyper-V | CVE-2025-53155 | Windows Hyper-V Elevation of Privilege Vulnerability | Important |
| Role: Windows Hyper-V | CVE-2025-49751 | Windows Hyper-V Denial of Service Vulnerability | Important |
| Role: Windows Hyper-V | CVE-2025-53723 | Windows Hyper-V Elevation of Privilege Vulnerability | Important |
| Role: Windows Hyper-V | CVE-2025-48807 | Windows Hyper-V Remote Code Execution Vulnerability | Critical |
| SQL Server | CVE-2025-49758 | Microsoft SQL Server Elevation of Privilege Vulnerability | Important |
| SQL Server | CVE-2025-24999 | Microsoft SQL Server Elevation of Privilege Vulnerability | Important |
| SQL Server | CVE-2025-53727 | Microsoft SQL Server Elevation of Privilege Vulnerability | Important |
| SQL Server | CVE-2025-49759 | Microsoft SQL Server Elevation of Privilege Vulnerability | Important |
| SQL Server | CVE-2025-47954 | Microsoft SQL Server Elevation of Privilege Vulnerability | Important |
| Storage Port Driver | CVE-2025-53156 | Windows Storage Port Driver Information Disclosure Vulnerability | Important |
| Web Deploy | CVE-2025-53772 | Web Deploy Remote Code Execution Vulnerability | Important |
| Windows Ancillary Function Driver for WinSock | CVE-2025-53718 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | Important |
| Windows Ancillary Function Driver for WinSock | CVE-2025-53134 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | Important |
| Windows Ancillary Function Driver for WinSock | CVE-2025-49762 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | Important |
| Windows Ancillary Function Driver for WinSock | CVE-2025-53147 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | Important |
| Windows Ancillary Function Driver for WinSock | CVE-2025-53154 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | Important |
| Windows Ancillary Function Driver for WinSock | CVE-2025-53137 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | Important |
| Windows Ancillary Function Driver for WinSock | CVE-2025-53141 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | Important |
| Windows Cloud Files Mini Filter Driver | CVE-2025-50170 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | Important |
| Windows Connected Devices Platform Service | CVE-2025-53721 | Windows Connected Devices Platform Service Elevation of Privilege Vulnerability | Important |
| Windows DirectX | CVE-2025-53135 | DirectX Graphics Kernel Elevation of Privilege Vulnerability | Important |
| Windows DirectX | CVE-2025-50172 | DirectX Graphics Kernel Denial of Service Vulnerability | Important |
| Windows Distributed Transaction Coordinator | CVE-2025-50166 | Windows Distributed Transaction Coordinator (MSDTC) Information Disclosure Vulnerability | Important |
| Windows File Explorer | CVE-2025-50154 | Microsoft Windows File Explorer Spoofing Vulnerability | Important |
| Windows GDI+ | CVE-2025-53766 | GDI+ Remote Code Execution Vulnerability | Critical |
| Windows Installer | CVE-2025-50173 | Windows Installer Elevation of Privilege Vulnerability | Important |
| Windows Kerberos | CVE-2025-53779 | Windows Kerberos Elevation of Privilege Vulnerability | Moderate |
| Windows Kernel | CVE-2025-49761 | Windows Kernel Elevation of Privilege Vulnerability | Important |
| Windows Kernel | CVE-2025-53151 | Windows Kernel Elevation of Privilege Vulnerability | Important |
| Windows Local Security Authority Subsystem Service (LSASS) | CVE-2025-53716 | Local Security Authority Subsystem Service (LSASS) Denial of Service Vulnerability | Important |
| Windows Media | CVE-2025-53131 | Windows Media Remote Code Execution Vulnerability | Important |
| Windows Message Queuing | CVE-2025-53145 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability | Important |
| Windows Message Queuing | CVE-2025-53143 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability | Important |
| Windows Message Queuing | CVE-2025-50177 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability | Critical |
| Windows Message Queuing | CVE-2025-53144 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability | Important |
| Windows NT OS Kernel | CVE-2025-53136 | NT OS Kernel Information Disclosure Vulnerability | Important |
| Windows NTFS | CVE-2025-50158 | Windows NTFS Information Disclosure Vulnerability | Important |
| Windows NTLM | CVE-2025-53778 | Windows NTLM Elevation of Privilege Vulnerability | Critical |
| Windows PrintWorkflowUserSvc | CVE-2025-53133 | Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability | Important |
| Windows Push Notifications | CVE-2025-53725 | Windows Push Notifications Apps Elevation of Privilege Vulnerability | Important |
| Windows Push Notifications | CVE-2025-53724 | Windows Push Notifications Apps Elevation of Privilege Vulnerability | Important |
| Windows Push Notifications | CVE-2025-50155 | Windows Push Notifications Apps Elevation of Privilege Vulnerability | Important |
| Windows Push Notifications | CVE-2025-53726 | Windows Push Notifications Apps Elevation of Privilege Vulnerability | Important |
| Windows Remote Desktop Services | CVE-2025-53722 | Windows Remote Desktop Services Denial of Service Vulnerability | Important |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-50157 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | Important |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-53153 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | Important |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-50163 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | Important |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-50162 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | Important |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-50164 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | Important |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-53148 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | Important |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-53138 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | Important |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-50156 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | Important |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-49757 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | Important |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-53719 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | Important |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-53720 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | Important |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-50160 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | Important |
| Windows Security App | CVE-2025-53769 | Windows Security App Spoofing Vulnerability | Important |
| Windows SMB | CVE-2025-50169 | Windows SMB Remote Code Execution Vulnerability | Important |
| Windows StateRepository API | CVE-2025-53789 | Windows StateRepository API Server file Elevation of Privilege Vulnerability | Important |
| Windows Subsystem for Linux | CVE-2025-53788 | Windows Subsystem for Linux (WSL2) Kernel Elevation of Privilege Vulnerability | Important |
| Windows Win32K – GRFX | CVE-2025-50161 | Win32k Elevation of Privilege Vulnerability | Important |
| Windows Win32K – GRFX | CVE-2025-53132 | Win32k Elevation of Privilege Vulnerability | Important |
| Windows Win32K – ICOMP | CVE-2025-50168 | Win32k Elevation of Privilege Vulnerability | Important |
Microsoft Patch Tuesday August 2025, August 2025 Patch Tuesday, Microsoft security updates August 2025, Patch Tuesday August 2025 fixes, Windows 10 KB5063709 update, Windows Server 2025 authentication vulnerability fix, Microsoft zero-day fix August 2025, Microsoft August 2025 cumulative updates, Microsoft Patch Tuesday schedule August 2025, August Patch Tuesday security flaws
Thank You for visiting Tech Uplifter!
Don’t forget to Subscribe to our Official Newsletter for latest updates.

